FAQ
Table of contents
- Why secureblue?
- Is secureblue immutable?
- Why not upstream your changes?
- Is this an install script?
- How do I update the system?
- Why is Flatpak included? Should I use Flatpak?
- Should I use Electron apps? Why don’t they work well with hardened_malloc?
- My fans are really loud, is this normal?
- How do I whitelist a module?
- Should I use Firejail?
- An app I use won’t start due to a malloc issue. How do I fix it?
- On secureblue half of my CPU cores are gone. Why is this?
- How do I install software?
- How do I install my VPN?
- How do I install Steam?
- How do I enable anti-cheat support?
- How do I install Docker?
- How do I enable printing?
- Why am I unable to start containers?
- How do I enable userns for other apps?
- Something broke! How do I rollback?
- Another security project has a feature that’s missing in secureblue, can you add it?
- Why are Bluetooth kernel modules disabled? How do I enable them?
- Why are upgrades so large?
- Why can’t I install new KDE themes?
- Why doesn’t my Xwayland app work?
- Why I can’t install nor use any GNOME user extensions?
- My clock is wrong, and it’s not getting automatically set. How do I fix this?
- How do I get notified of new releases?
- What do the GitHub releases involve?
- Why don’t my AppImages work?
- Why don’t KDE Vaults work?
- How do I provision signed Distroboxes?
- Why won’t Trivalent start when Bubblejailed?
- Why won’t Trivalent start on Nvidia?
- Why don’t some websites that require JIT/WebAssembly work in Trivalent even with the V8 Optimizer toggle enabled?
- Why don’t extensions work in Trivalent?
- Why does Trivalent log me out of all sites by default?
- How do I customize secureblue?
- How do I add a repo?
- How do I install proprietary codecs?
- How do I change my DE?
- Why doesn’t DRM content (spotify, netflix etc.) work in Trivalent?
- How do I enable kernel modules?
- Why am I being asked to enroll a Secure Boot key?
- Why does secureblue include Homebrew?
- Does secureblue use “linux-hardened”?
- Why is my splash screen disabled on KDE?
- Why is my secureblue virtual machine integration broken?
Why secureblue?
secureblue is a collaborative effort to ship a maximally secure Linux operating system. It leverages bootable container technology to build on top of Fedora Atomic, avoiding the need to become a distro in the traditional sense. secureblue has benefitted massively by not being a distro, and instead shipping as bootable OCI container images. This has meant a ton of overhead is taken care of for us by Fedora. We don’t need general repos or packaging, except for a handful of specific packages (Trivalent, hardened_malloc, etc). The Fedora Atomic ecosystem is also rich in tooling and automation (see: BlueBuild), plus the backdrop of robust container technology that already exists. All of this has largely enabled us to focus our energy on improving secureblue’s hardening and UX, developing Trivalent, and building out userspace SELinux policies.
Is secureblue immutable?
“Immutable” is an old misnomer for atomic systems. It gives the impression that users can’t modify or tinker with their system, which is not the case. While directories like /usr are mounted read-only by default, settings and configurations can be easily overriden with changes in /etc, which is not mounted read-only. This is in addition to the fact that /usr is mutated with every deployment that is staged and booted via any rpm-ostree operation (like upgrading, installing a new package, etc). As such, secureblue is not immutable.
Why not upstream your changes?
When possible, we do upstream our changes. In particular, we have contributed several findings and fixes to KDE. However, it’s important to note that many of the changes we make are not possible to upstream, generally due to upstream not desiring them. This is for good reason. Many of the changes secureblue makes will necessarily break someone’s use case by default. Otherwise, secureblue could just submit all of our changes upstream to Fedora. Take AppImage support as an example. AppImages depend on the suid-root, deprecated, unmaintained fuse2 interface. They also encourage users to follow the security antipattern of downloading and executing binaries from the browser. Yet, since AppImages are widely used, Fedora can’t remove support for them. secureblue is willing to make these kinds of changes by default to improve security, with mechanisms available for users to re-enable support if needed for their use cases.
Is this an install script?
No. secureblue is not an install script, nor an add-on to a Fedora installation, nor a distro in the traditional sense. It is a set of bootable container images shipped via GitHub’s container registry. These images are rebuilt daily and pushed to GitHub’s container registry. These images are then pulled in by rpm-ostree, which stages updates as a pending deployment for the next boot. To view information about your current local deployments and remotes, run rpm-ostree status.
How do I update the system?
All system updates are automatic, running on at least a daily cadence. This includes automatic updates for rpm-ostree, brew, flatpak, and podman. If the system is over 1 week out of date (for example in the event of update failures), the user will be notified and pointed to the right command to run to manually upgrade.
Why is Flatpak included? Should I use Flatpak?
Consult our Flatpak article.
Should I use Electron apps? Why don’t they work well with hardened_malloc?
Consult this discussion
My fans are really loud, is this normal?
During rpm-ostree operations, it’s normal. Outside of that, make sure you followed the NVIDIA steps in the post-install instructions if you’re using an NVIDIA GPU.
How do I whitelist a module?
secureblue prevents numerous modules from loading to reduce attack surface. If there’s a particular module you need, run ujust override-enable-module mod_name. To undo this, run ujust override-reset-module mod_name.
Should I use Firejail?
No, use bubblejail if there’s no Flatpak available for an app that you want to sandbox. Note that this requires enabling unconfined user namespaces, which is a security degradation.
An app I use won’t start due to a malloc issue. How do I fix it?
- For Flatpaks, remove the
LD_PRELOADenvironment variable via Flatseal. To re-enable hardened_malloc for the respective Flatpak, replace the removed variable. - For layered packages and packages installed via brew, run the application with
ujust with-standard-malloc APP. This starts the app without hardened_malloc only once, it does not disable hardened_malloc for the app persistently.
On secureblue half of my CPU cores are gone. Why is this?
mitigations=auto,nosmt is set on secureblue. This means that if your CPU is vulnerable to attacks that utilize Simultaneous Multithreading, SMT will be disabled. There are several other kargs secureblue sets that may also trigger this behavior, including nosmt=force, and l1tf=full,force.
How do I install software?
- Check if it’s already installed using
rpm -qa | grep x - For GUI packages, you can install the Flatpak if available using the Software store or using
flatpak install. You can browse this catalogue of Flatpaks to discover the available packages. - For CLI packages, you can install from brew if available using
brew install. You can browse this catalogue of Homebrew Formulaes to discover the available formulaes. - If a package isn’t available via the other two options, or if a package requires greater system integration,
rpm-ostree installcan be used to layer rpms directly into your subsequent deployments.
You can add the unfiltered Flathub repo with ujust enable-flathub-unfiltered.
How do I install my VPN?
To install a standalone VPN app, use ujust install-vpn.
Alternatively, you can download a WireGuard profile config from your VPN provider’s website and import it via the system network settings menu. Below are the steps for GNOME.
- Navigate to the “Network” tab in GNOME settings.
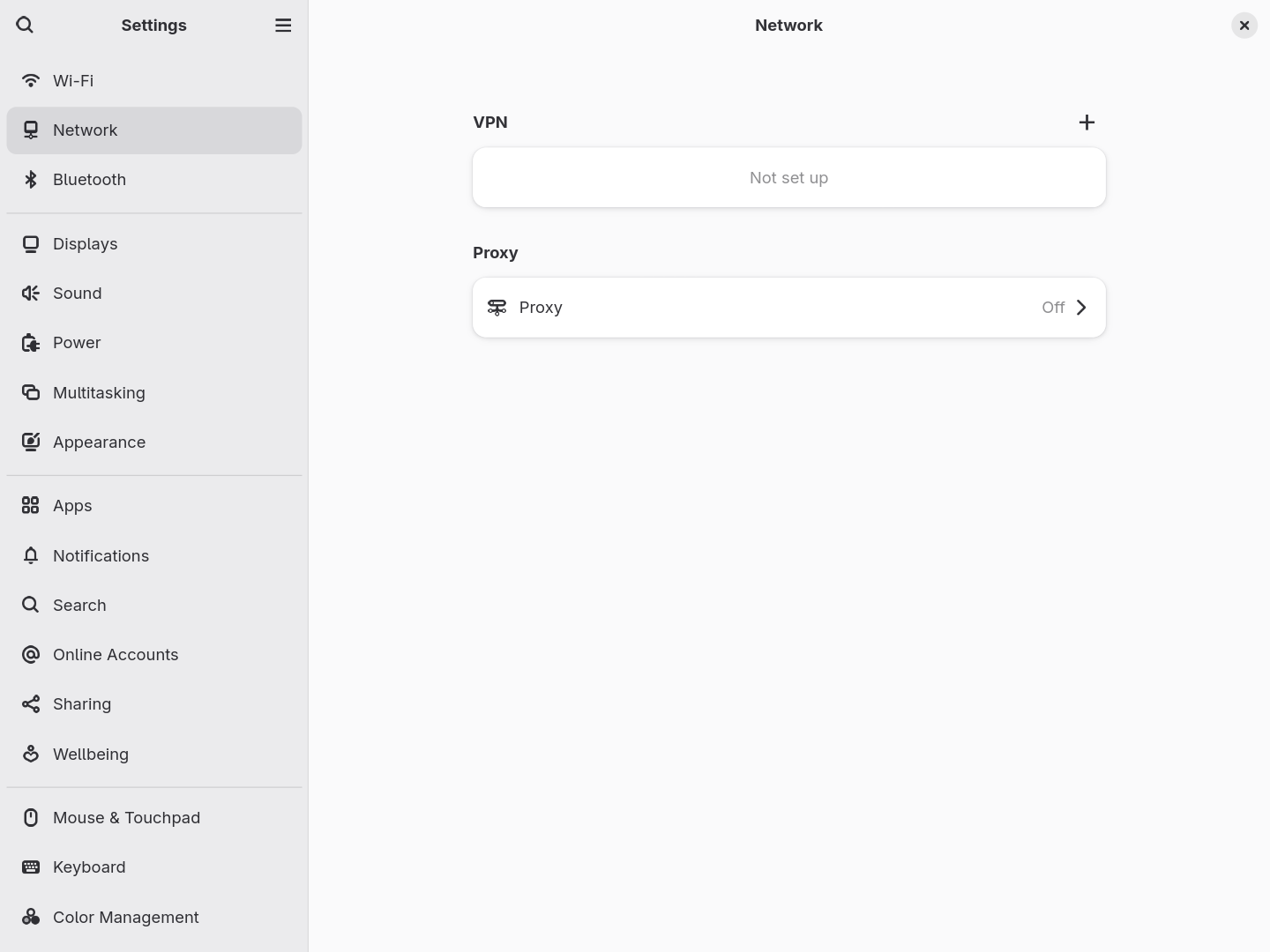
- Click the “+” button to add a new VPN connection.
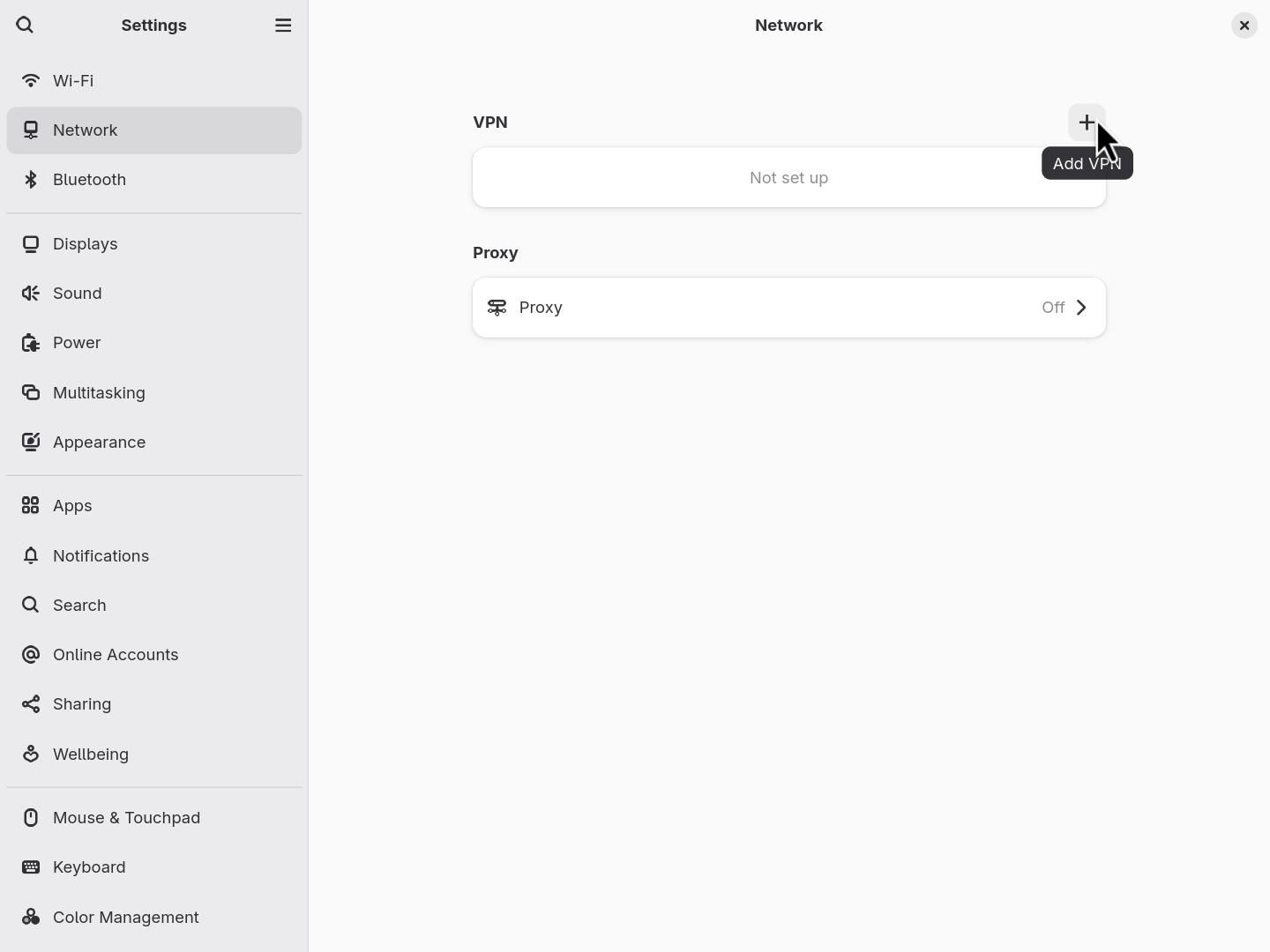
- Click “Import from file…” and use the file chooser to select the VPN config file you downloaded from your VPN provider.
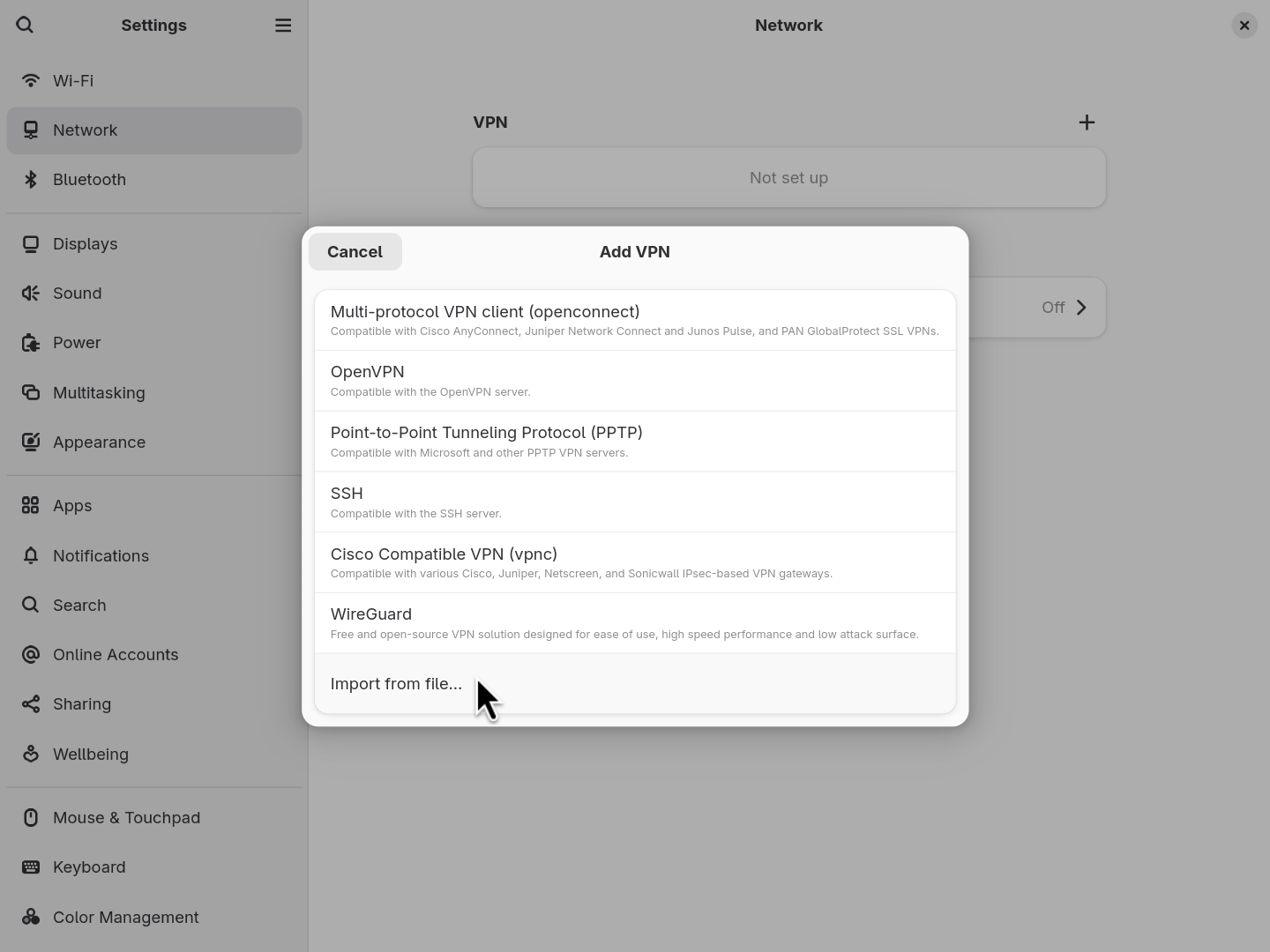
- Click the “Add” button, and your VPN will now be accessible through the system network settings.
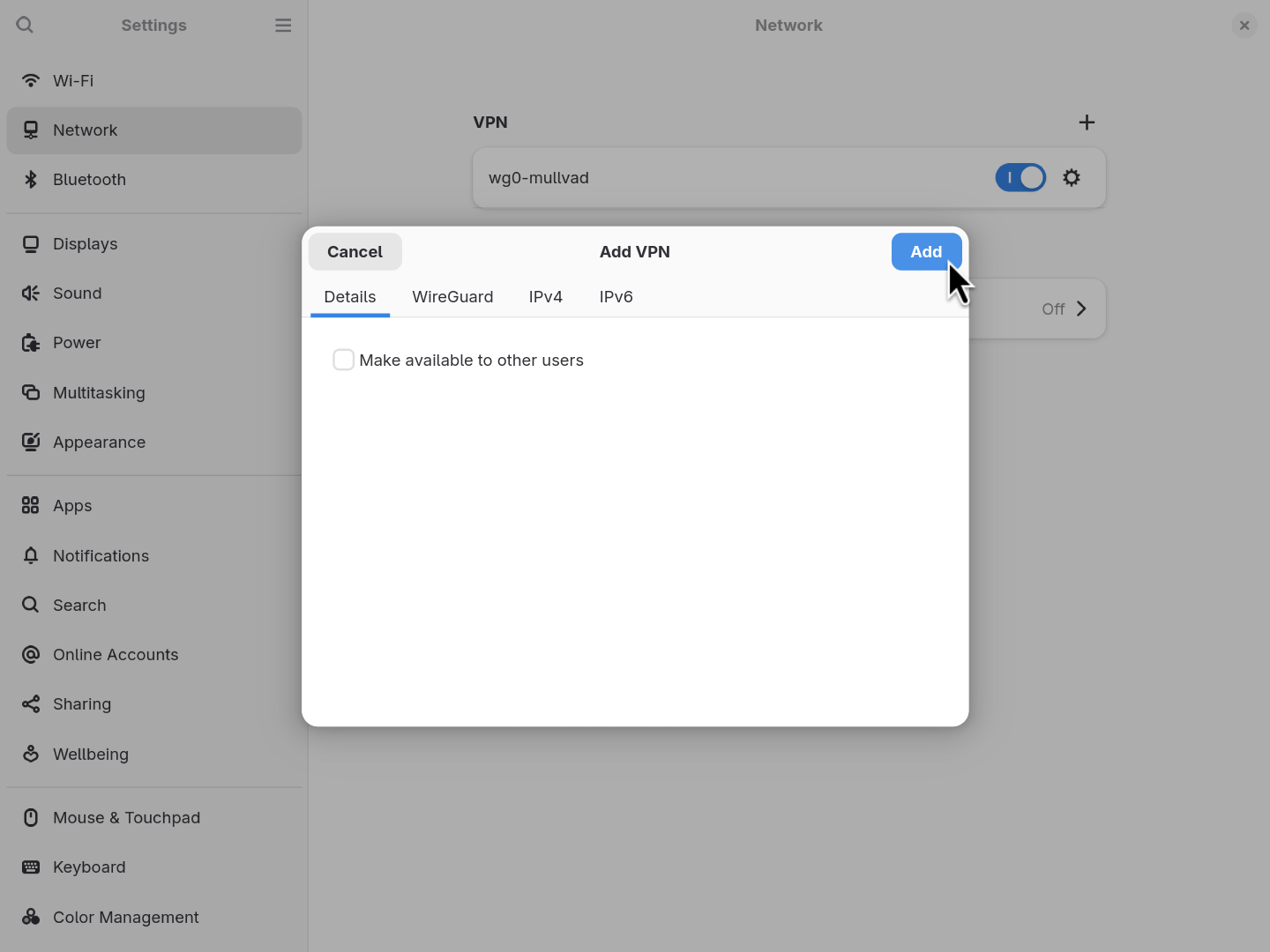
Note
If you get an error that says "Cannot Import VPN", that is likely because the name of the WireGuard configuration file is too long. GNOME Settings will only accept WireGuard configuration files with filenames 15 characters or less.
How do I install Steam?
ujust install-steam
How do I enable anti-cheat support?
Note
Kernel-level anti-cheat solutions are generally unsupported on desktop Linux.
Anti-cheat solutions typically require process tracing to work - the ability to monitor syscalls (and other signals) from other processes. On Linux, process tracing is controlled by the kernel.yama.ptrace_scope kernel parameter. By default, secureblue doesn’t allow ptrace attachment at all, addressing basic security concerns. The command below toggles between this restrictive default setting where ptrace_scope is set to 3, breaking anti-cheat software, and a much less restrictive setting where ptrace_scope is set to 1, which allows parent processes to trace child processes, enabling some anti-cheat solutions to work.
ujust toggle-anticheat-support
The ujust above is aliased as toggle-ptrace-scope. You must reboot your computer after running it.
How do I install Docker?
ujust install-docker
Similarly, you can uninstall Docker with:
ujust uninstall-docker
How do I enable printing?
To enable printing using CUPS, run ujust toggle-cups. Note that this enables printing support, but still leaves printer discovery disabled for security reasons. The CUPS printer discovery service increases attack surface significantly and has a recent history of severe vulnerabilities.
Why am I unable to start containers?
Software such as Podman and Distrobox need to be able to create user namespaces to work without root. The privilege to do so is denied by default in secureblue, but can be granted by running the following command:
ujust toggle-container-domain-userns-creation
Trying to start a container without first enabling the ability toggled by the ujust above will result in an OCI permission denied error, but beware that enabling it results in a security degradation. Consult our user namespaces article for more details.
How do I enable userns for other apps?
The following command will toggle the ability of processes in the unconfined SELinux domain to create user namespaces. It’s necessary for any apps that require this feature, such as bubblewrap when it isn’t SUID-root.
ujust toggle-unconfined-domain-userns-creation
Attempting to bubblewrap a program without first enabling the ability toggled by the ujust above will result in a bwrap: Creating new namespace failed: Permission denied error, but beware that enabling it results in a security degradation. Consult our user namespaces article for more details.
Something broke! How do I rollback?
Each rpm-ostree operation generates and stages a new deployment, which includes the creation of a new GRUB entry at position 0. To boot into the previous deployment, simply select the GRUB entry at position 1. As a preventative measure, you can ensure you always have a known-good deployment available by pinning an existing deployment.
Another security project has a feature that’s missing in secureblue, can you add it?
First, check our features list to see whether it already lists an equivalent or better feature. If it doesn’t, open a new GitHub issue.
Why are Bluetooth kernel modules disabled? How do I enable them?
Bluetooth has a long and consistent history of security issues. However, if you still need it, run:
ujust toggle-bluetooth-modules
Why are upgrades so large?
This is an issue with rpm-ostree image-based systems generally, and not specific to secureblue. Ideally, upgrades would come in the form of a zstd-compressed container diff, but it’s not there yet. Check out this upstream issue for more information.
Why can’t I install new KDE themes?
The functionality that provides this, called GHNS, is disabled by default due to the risk posed by the installation of potentially damaging or malicious scripts. This has caused real damage.
If you still want to enable this functionality, run:
ujust toggle-ghns
Why doesn’t my Xwayland app work?
Xwayland is disabled by default on GNOME, KDE Plasma, and Sway. If you need it, run:
ujust toggle-xwayland
Why I can’t install nor use any GNOME user extensions?
This is because support for installing & using them has been intentionally disabled by default in secureblue. Only GNOME system extensions are trusted, if they are installed.
To enable support for installing GNOME user extensions, you can run ujust command:
ujust toggle-gnome-extensions
My clock is wrong, and it’s not getting automatically set. How do I fix this?
If your system time is off by an excessive amount due to rare conditions like a CMOS reset, your network will not connect. A one-time manual reset will fix this. This should never be required except under very rare circumstances.
For more technical detail, see issue #268
How do I get notified of new releases?
To subscribe to release notifications, on the secureblue GitHub page, click “Watch”, and then “Custom”, and select Releases like so:
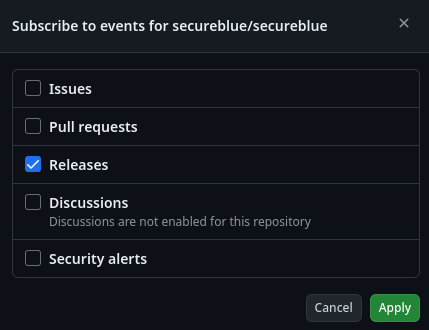
If you prefer to use an Atom feed, supported by many RSS clients, you can use the feed provided by GitHub.
What do the GitHub releases involve?
Substantial testing for new changes is done in the staging and next branches. However, once a commit is merged into live, a new set of builds is immediately generated and deployed. As such, the GitHub releases are an informational measure to track progress and communicate changes to users. This is only the case for the secureblue main repo, it isn’t the case for Trivalent. For Trivalent, GitHub releases correspond to RPM releases to the RPM repo.
Why don’t my AppImages work?
AppImages depend on fuse2, which is unmaintained and depends on a SUID root binary. For this reason, fuse2 support is removed by default. It’s strongly recommended that you find alternative mechanisms to install your applications (Flatpak, Distrobox, etc.). If you can’t find an alternative and still need fuse2, you can add it back by layering something that depends on it.
For example:
rpm-ostree install funionfs
Why don’t KDE Vaults work?
Similar to the AppImage FAQ, the KDE Vault default backend cryfs depends on fuse2. For this reason, it’s recommended that you migrate to an alternative that doesn’t depend on fuse2, for example fscrypt. If you don’t want to do so, you can add fuse2 back by layering something that depends on it, as described in the AppImage FAQ.
How do I provision signed Distroboxes?
ujust distrobox-assemble
Why won’t Trivalent start when Bubblejailed?
bubblejail shouldn’t be used on Trivalent, there are issues reported with the pairing and removing the bubblejail config after it is applied can be difficult. It should also be noted that applying additional sandboxing may interfere with chromium’s own internal sandbox, so it may end up reducing security.
Why won’t Trivalent start on Nvidia?
On some Nvidia machines, Trivalent defaults to the X11 backend. Since secureblue disables Xwayland by default, this means that you will need to run ujust toggle-xwayland and reboot, for Trivalent to work.
Why don’t some websites that require JIT/WebAssembly work in Trivalent even with the V8 Optimizer toggle enabled?
This is an upstream bug that prevents V8 optimization settings from being applied to iframes embedded within a parent website. As a result, WebAssembly may not function on services that use a separate URL for their content delivery network or other included domains, such as VSCode Web (https://github.dev). To make VSCode Web work properly, you need to manually allow V8 optimizations for the CDN by adding https://[*.]vscode-cdn.net to your list of trusted websites.
Why don’t extensions work in Trivalent?
Extensions in Trivalent are disabled by default, for security reasons, it is not advised to use them. If you want content/ad blocking, that is already built into Trivalent and enabled by default. If you require extensions, you can re-enable them by disabling the Disable Extensions toggle under chrome://settings/security, then restart your browser (this toggle is per-profile).
If the extension you installed doesn’t work, it is likely because it requires WebAssembly (WASM) for some cryptographic library or some other optimizations (this is the case with the Bitwarden extension). To re-enable JavaScript JIT and WASM for an extension, visit chrome://extensions, under the extension with the issues, go Details -> Site Settings, then scroll to V8 Optimizer and flip to allow. If the extension continues to not work, try reinstalling the extension.
Why does Trivalent log me out of all sites by default?
It shouldn’t, this is a bug related to Chromium’s Network Service Sandbox where cookies are either cleared or become inaccessible when the browser is closed. If you experience this, navigate to chrome://settings/security, at the bottom you will see a Hardening section and within it a toggle Network Service Sandbox, flip this to off and restart your browser.
How do I customize secureblue?
If you want to add your own customizations on top of secureblue that go beyond installing packages, you are advised strongly against forking. Instead, create a repo for your own image by using the BlueBuild template, then change your base-image to a secureblue image. This allows you to apply your customizations to secureblue in a concise and maintainable way, without the need to constantly sync with upstream. For local development, building locally is the recommended approach.
How do I add a repo to secureblue?
The process of adding a repository to secureblue is the same as on Fedora
How do I install proprietary codecs?
There is no need, they are already included in the image.
How do I change my DE?
Choose whatever you like from the available options by running ujust rebase-secureblue.
Why doesn’t DRM content (spotify, netflix etc.) work in Trivalent?
DRM-protected content is available in trivalent, however it is disabled by default. Visit chrome://settings/content/protectedContent and select “Sites can play protected content”.
How do I enable kernel modules?
Some functionality requires you to enable extra kernel modules that are disabled by default in secureblue. Modules can be enabled by running ujust override-enable-module. For instance, mounting SMB shares requires the cifs and netfs kernel modules. To load them, simply run ujust override-enable-module cifs and ujust override-enable-module netfs then reboot.
Why am I being asked to enroll a Secure Boot key?
As part of a move to unify our supply chain, secureblue is moving off of uBlue’s kernel cache and akmods. This has both practical and security advantages, and paves the way towards further kernel security improvements in the future. This change includes a transition to a new secureblue Secure Boot key. You must enroll this new key to prevent issues loading kernel modules:
ujust enroll-secureblue-secure-boot-key
Why does secureblue include Homebrew?
Homebrew is a cross-platform package manager, originally for macOS that allows users on Atomic systems to install CLI tools without layering and rebooting their system. It also brings with it a recent independent security audit and subsequent actions taken in response to security findings uncovered by that audit.
Does secureblue use “linux-hardened”?
“linux-hardened” is the brand name for a specific set of kernel patches and builds on top of the mainline kernel, used by some distributions. secureblue doesn’t use this kernel. Instead, we apply runtime configuration changes on top of Fedora’s kernel. We can accomplish much but not all of what linux-hardened accomplishes using this approach. In the future, we plan to build our own kernel with patches on top of Fedora’s kernel, including the OpenPAX patches. However, even today there are some important ways in which our approach is preferable. For example, linux-hardened completely disables unprivileged user namespaces. This means that to use flatpaks or chromium-based browsers, suid-root binaries are required. This is a significant security degradation. secureblue on the other hand implements SELinux-confined unprivileged user namespaces, restricting them by default but allowing them for Flatpaks and Trivalent to enable their operation without suid-root.
Why is my splash screen disabled on KDE?
The KDE splash screen is currently broken if XWayland is disabled (which is the default on secureblue), due to an upstream bug. secureblue automatically disables it for every user to work around this. If you don’t want the splash screen to be automatically disabled, run the following command:
systemctl disable --user disable-kde-splash.service
Why is my virtual machine integration broken?
In order to use SPICE integration with a secureblue guest, such as the shared clipboard and automatic display resolution setting, you must enable XWayland:
ujust toggle-xwayland